Microsoft Monthly Security Update (October 2025)
RISK: Medium Risk
TYPE: Operating Systems - Windows OS
Microsoft has released monthly security update for their products:
| Vulnerable Product | Risk Level | Impacts | Notes |
| Azure |  Medium Risk Medium Risk | Elevation of Privilege Remote Code Execution Spoofing | |
| Windows |  Medium Risk Medium Risk | Elevation of Privilege Information Disclosure Security Restriction Bypass Remote Code Execution Spoofing Denial of Service Data Manipulation | CVE-2025-59230 is being exploited in the wild. Improper access control in Windows Remote Access Connection Manager allows an authorized attacker to elevate privileges locally.
CVE-2025-24990 is being exploited in the wild. Microsoft is aware of vulnerabilities in the third party Agere Modem driver that ships natively with supported Windows operating systems. This is an announcement of the upcoming removal of ltmdm64.sys driver. The driver has been removed in the October cumulative update.
Proof of Concept exploit code is publicly available for CVE-2025-24052 . Microsoft is aware of vulnerabilities in the third party Agere Modem driver that ships natively with supported Windows operating systems. This is an announcement of the upcoming removal of ltmdm64.sys driver. The driver has been removed in the October cumulative update.
CVE-2025-47827 is being exploited in the wild. In IGEL OS before 11, Secure Boot can be bypassed because the igel-flash-driver module improperly verifies a cryptographic signature. Ultimately, a crafted root filesystem can be mounted from an unverified SquashFS image. |
| Server Software |  Medium Risk Medium Risk | Elevation of Privilege Spoofing | |
| Developer Tools |  Medium Risk Medium Risk | Elevation of Privilege Information Disclosure Security Restriction Bypass | |
| Extended Security Updates (ESU) |  Medium Risk Medium Risk | Elevation of Privilege Information Disclosure Remote Code Execution Spoofing Denial of Service Data Manipulation Security Restriction Bypass | CVE-2025-59230 is being exploited in the wild. Improper access control in Windows Remote Access Connection Manager allows an authorized attacker to elevate privileges locally.
CVE-2025-24990 is being exploited in the wild. Microsoft is aware of vulnerabilities in the third party Agere Modem driver that ships natively with supported Windows operating systems. This is an announcement of the upcoming removal of ltmdm64.sys driver. The driver has been removed in the October cumulative update.
Proof of Concept exploit code is publicly available for CVE-2025-24052 . Microsoft is aware of vulnerabilities in the third party Agere Modem driver that ships natively with supported Windows operating systems. This is an announcement of the upcoming removal of ltmdm64.sys driver. The driver has been removed in the October cumulative update.
CVE-2025-47827 is being exploited in the wild. In IGEL OS before 11, Secure Boot can be bypassed because the igel-flash-driver module improperly verifies a cryptographic signature. Ultimately, a crafted root filesystem can be mounted from an unverified SquashFS image. |
| System Center |  Medium Risk Medium Risk | Elevation of Privilege Denial of Service | |
| Microsoft Office |  Medium Risk Medium Risk | Remote Code Execution Information Disclosure Denial of Service | |
| SQL Server | 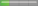 Low Risk Low Risk | Spoofing | |
| Apps |  Medium Risk Medium Risk | Elevation of Privilege Spoofing | |
| Open Source Software | 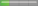 Low Risk Low Risk | Spoofing |
Number of 'Extremely High Risk' product(s): 0
Number of 'High Risk' product(s): 0
Number of 'Medium Risk' product(s): 8
Number of 'Low Risk' product(s): 2
Evaluation of overall 'Risk Level': Medium Risk
Impact
- Remote Code Execution
- Denial of Service
- Data Manipulation
- Information Disclosure
- Security Restriction Bypass
- Elevation of Privilege
- Spoofing
System / Technologies affected
- Azure
- Windows
- Server Software
- Developer Tools
- Extended Security Updates (ESU)
- System Center
- Microsoft Office
- SQL Server
- Apps
- Open Source Software
Solutions
Before installation of the software, please visit the vendor web-site for more details.
- Apply fixes issued by the vendor.

沒有留言:
發佈留言