Microsoft Monthly Security Update (September 2023)
Release Date: 13 Sep 2023
RISK: High Risk
TYPE: Operating Systems - Windows OS

Microsoft has released monthly security update for their products:
| Vulnerable Product | Risk Level | Impacts | Notes |
| Browser | 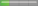 Low Risk Low Risk | ||
| Windows | 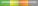 High Risk High Risk | Elevation of Privilege Denial of Service Information Disclosure Remote Code Execution Security Restriction Bypass | CVE-2023-36802 is being exploited in the wild. The vulnerability can be exploited to local privilege elevation vulnerability that allows attackers to gain SYSTEM privileges. |
| Extended Security Updates (ESU) |  Medium Risk Medium Risk | Elevation of Privilege Information Disclosure Denial of Service | |
| Azure |  Medium Risk Medium Risk | Elevation of Privilege Remote Code Execution | |
| Microsoft Office | 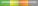 High Risk High Risk | Security Restriction Bypass Information Disclosure Elevation of Privilege Spoofing Remote Code Execution | CVE-2023-36761 is being exploited in the wild. The vulnerability can be used to steal NTLM hashes when opening a document, including in the preview pane. These NTLM hashes can be cracked or used in NTLM Relay attacks to gain access to the account. |
| Developer Tools |  Medium Risk Medium Risk | Elevation of Privilege Remote Code Execution Denial of Service | |
| Exchange Server |  Medium Risk Medium Risk | Spoofing Remote Code Execution Information Disclosure | |
| Apps |  Medium Risk Medium Risk | Remote Code Execution | |
| Microsoft Dynamics | 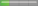 Low Risk Low Risk | Spoofing | |
| System Center |  Medium Risk Medium Risk | Security Restriction Bypass |
Number of 'Extremely High Risk' product(s): 0
Number of 'High Risk' product(s): 2
Number of 'Medium Risk' product(s): 6
Number of 'Low Risk' product(s): 2
Evaluation of overall 'Risk Level': High Risk
Impact
- Denial of Service
- Elevation of Privilege
- Information Disclosure
- Remote Code Execution
- Spoofing
- Security Restriction Bypass
System / Technologies affected
- Browser
- Windows
- Extended Security Updates (ESU)
- Azure
- Microsoft Office
- Developer Tools
- Exchange Server
- Apps
- Microsoft Dynamics
- System Center
Solutions
Before installation of the software, please visit the vendor web-site for more details.
- Apply fixes issued by the vendor.

沒有留言:
發佈留言