Microsoft Monthly Security Update (February 2023)
RISK: Extremely High Risk
TYPE: Operating Systems - Windows OS

[Updated on 2023-03-07]
Proof of Concept exploit code is publicly available for CVE-2023-21716, affecting Microsoft Word. The vulnerability could be exploited by previewing a malicious RTF document and execute arbitrary code after memory corruption.
Microsoft has released monthly security update for their products:
| Vulnerable Product | Risk Level | Impacts | Notes |
| SQL Server |  Medium Risk Medium Risk | Remote Code Execution Spoofing | |
| Windows | 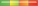 Extremely High Risk Extremely High Risk | Remote Code Execution Elevation of Privilege Denial of Service Information Disclosure | Exploit in the wild |
| Extended Security Updates (ESU) | 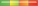 Extremely High Risk Extremely High Risk | Remote Code Execution Elevation of Privilege Denial of Service Information Disclosure | Exploit in the wild |
| Azure |  Medium Risk Medium Risk | Elevation of Privilege Information Disclosure Remote Code Execution Spoofing | |
| Microsoft Dynamics |  Medium Risk Medium Risk | Remote Code Execution Spoofing | |
| Browser |  Medium Risk Medium Risk | Spoofing Data Manipulation Remote Code Execution | |
| Exchange Server |  Medium Risk Medium Risk | Remote Code Execution | |
| Microsoft Office | 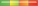 Extremely High Risk Extremely High Risk | Spoofing Remote Code Execution Elevation of Privilege Information Disclosure Security Restriction Bypass | Exploit in the wild
Proof of Concept exploit code Is publicly available for CVE-2023-21716 |
| Developer Tools |  Medium Risk Medium Risk | Elevation of Privilege Denial of Service Remote Code Execution | |
| Apps |  Medium Risk Medium Risk | Remote Code Execution | |
| System Center |  Medium Risk Medium Risk | Elevation of Privilege Security Restriction Bypass | |
| Device |  Medium Risk Medium Risk | Information Disclosure |
Number of 'Extremely High Risk' product(s): 3
Number of 'High Risk' product(s): 0
Number of 'Medium Risk' product(s): 9
Number of 'Low Risk' product(s): 0
Evaluation of overall 'Risk Level': Extremely High Risk
Impact
- Denial of Service
- Remote Code Execution
- Spoofing
- Elevation of Privilege
- Information Disclosure
- Data Manipulation
- Security Restriction Bypass
System / Technologies affected
- SQL Server
- Windows
- Extended Security Updates (ESU)
- Azure
- Microsoft Dynamics
- Browser
- Exchange Server
- Microsoft Office
- Developer Tools
- Apps
- System Center
- Device
Solutions
Before installation of the software, please visit the vendor web-site for more details.
- Apply fixes issued by the vendor.

沒有留言:
發佈留言