Microsoft Edge 多個漏洞
風險: 中度風險
類型: 用戶端 - 瀏覽器
於 Microsoft Edge 發現多個漏洞。遠端攻擊者可利用這些漏洞,於目標系統觸發阻斷服務狀況及遠端執行任意程式碼。
影響
- 阻斷服務
- 遠端執行程式碼
受影響之系統或技術
- Microsoft Edge 143.0.3650.80 之前的版本
解決方案
在安裝軟體之前,請先瀏覽供應商之網站,以獲得更多詳細資料。
安裝軟件供應商提供的修補程式:
- 更新至 143.0.3650.80 或之後版本
風險: 中度風險
類型: 用戶端 - 瀏覽器
於 Microsoft Edge 發現多個漏洞。遠端攻擊者可利用這些漏洞,於目標系統觸發阻斷服務狀況及遠端執行任意程式碼。
在安裝軟體之前,請先瀏覽供應商之網站,以獲得更多詳細資料。
安裝軟件供應商提供的修補程式:
RISK: Medium Risk
TYPE: Clients - Browsers
Multiple vulnerabilities were identified in Microsoft Edge. A remote attacker could exploit some of these vulnerabilities to trigger denial of service condition and remote code execution on the targeted system.
Before installation of the software, please visit the software vendor web-site for more details.
Apply fixes issued by the vendor:
風險: 中度風險
類型: 伺服器 - 其他伺服器
於 React 發現多個漏洞。遠端攻擊者可利用這些漏洞,於目標系統觸發阻斷服務狀況及洩露敏感資料。
受影響的 React 版本:
詳情請參閱以下連結:
在安裝軟體之前,請先瀏覽供應商之網站,以獲得更多詳細資料。
安裝供應商提供的修補程式:
RISK: Medium Risk
TYPE: Servers - Other Servers
Multiple vulnerabilities were identified in React. A remote attacker could exploit some of these vulnerabilities to trigger denial of service condition and sensitive information disclosure on the targeted system.
For affected versions of React:
The vulnerability is present in versions 19.0.0, 19.0.1, 19.0.2, 19.1.0, 19.1.1, 19.1.2, 19.1.2, 19.2.0, 19.2.1 and 19.2.2 of:
For detail, please refer to the links below:
Before installation of the software, please visit the vendor web-site for more details.
Apply fixes issued by the vendor:
風險: 中度風險
類型: 伺服器 - 網站伺服器
於Apache Struts發現一個漏洞,遠端使用者可利用此漏洞,於目標系統觸發阻斷服務狀況。
在安裝軟體之前,請先瀏覽軟體供應商之網站,以獲得更多詳細資料。
處理方法:
透過以下方法以緩解此漏洞的影響:
RISK: Medium Risk
TYPE: Servers - Web Servers
A vulnerability was identified in Apache Struts, a remote user can exploit this vulnerability to trigger Denial of Service condition on the targeted system.
Before installation of the software, please visit the software manufacturer web-site for more details.
Workaround:
Mitigate the vulnerability by the following workaround:
Define a temporary folder used to store uploaded files with limited size or on the dedicated volume which won't affect system files. Or disable file upload support in the framework if not used.
風險: 中度風險
類型: 伺服器 - 其他伺服器
於 GitLab 發現多個漏洞。遠端攻擊者可利用這些漏洞,於目標系統觸發跨網站指令碼、阻斷服務狀況、洩露敏感資料及繞過保安限制。
在安裝軟體之前,請先瀏覽供應商之網站,以獲得更多詳細資料。
安裝供應商提供的修補程式:
RISK: Medium Risk
TYPE: Servers - Other Servers
Multiple vulnerabilities were identified in GitLab. A remote attacker could exploit some of these vulnerabilities to trigger cross-site scripting, denial of service condition, sensitive information disclosure and security restriction bypass on the targeted system.
Before installation of the software, please visit the vendor web-site for more details.
Apply fixes issued by the vendor:
風險: 中度風險
類型: 用戶端 - 瀏覽器
於 Google Chrome 發現多個漏洞。遠端攻擊者可利用這些漏洞,於目標系統觸發阻斷服務狀況及遠端執行任意程式碼。
在安裝軟體之前,請先瀏覽供應商之網站,以獲得更多詳細資料。
安裝軟件供應商提供的修補程式:
RISK: Medium Risk
TYPE: Clients - Browsers
Multiple vulnerabilities were identified in Google Chrome. A remote attacker could exploit some of these vulnerabilities to trigger denial of service condition and remote code execution on the targeted system.
Before installation of the software, please visit the software vendor web-site for more details.
Apply fixes issued by the vendor:
風險: 中度風險
類型: 伺服器 - 互聯網應用伺服器
於 Jenkins 發現多個漏洞。遠端攻擊者可利用這些漏洞,於目標系統觸發仿冒、阻斷服務狀況及洩露敏感資料。
在安裝軟體之前,請先瀏覽供應商之網站,以獲得更多詳細資料。
安裝供應商提供的修補程式:
RISK: Medium Risk
TYPE: Servers - Internet App Servers
Multiple vulnerabilities were identified in Jenkins. A remote attacker could exploit some of these vulnerabilities to trigger spoofing, denial of service condition and sensitive information disclosure on the targeted system.
Before installation of the software, please visit the vendor web-site for more details.
Apply fixes issued by the vendor:
風險: 中度風險
類型: 用戶端 - 瀏覽器
於 Mozilla Thunderbird 發現多個漏洞。遠端攻擊者可利用這些漏洞,於目標系統觸發仿冒、權限提升、遠端執行任意程式碼及繞過保安限制。
以下版本之前的版本﹕
在安裝軟體之前,請先瀏覽供應商之官方網站,以獲得更多詳細資料。
更新至版本:
RISK: Medium Risk
TYPE: Clients - Browsers
Multiple vulnerabilities were identified in Mozilla Thunderbird. A remote attacker could exploit some of these vulnerabilities to trigger spoofing, elevation of privilege, remote code execution and security restriction bypass on the targeted system.
Versions prior to:
Before installation of the software, please visit the vendor web-site for more details.
Apply fixes issued by the vendor:
風險: 中度風險
類型: 用戶端 - 辦公室應用
Adobe已為產品提供本月保安更新:
| 受影響產品 | 風險程度 | 影響 | 備註 | 詳情(包括 CVE) |
| Adobe ColdFusion |  中度風險 中度風險 | 遠端執行程式碼 權限提升 | APSB25-105 | |
| Adobe Experience Manager |  中度風險 中度風險 | 跨網站指令碼 遠端執行程式碼 資料洩露 | APSB25-115 | |
| Adobe DNG Software Development Kit (SDK) |  中度風險 中度風險 | 遠端執行程式碼 資料洩露 | APSB25-118 | |
| Adobe Acrobat and Reader |  中度風險 中度風險 | 遠端執行程式碼 繞過保安限制 | APSB25-119 | |
| Adobe Creative Cloud Desktop Application |  中度風險 中度風險 | 阻斷服務 | APSB25-120 |
「極高度風險」產品數目:0
「高度風險」產品數目:0
「中度風險」產品數目:5
「低度風險」產品數目:0
整體「風險程度」評估:中度風險
在安裝軟體之前,請先瀏覽供應商之網站,以獲得更多詳細資料。
RISK: Medium Risk
TYPE: Clients - Productivity Products
Adobe has released monthly security update for their products:
| Vulnerable Product | Risk Level | Impacts | Notes | Details (including CVE) |
| Adobe ColdFusion |  Medium Risk Medium Risk | Remote Code Execution Elevation of Privilege | APSB25-105 | |
| Adobe Experience Manager |  Medium Risk Medium Risk | Cross-site Scripting Remote Code Execution Information Disclosure | APSB25-115 | |
| Adobe DNG Software Development Kit (SDK) |  Medium Risk Medium Risk | Remote Code Execution Information Disclosure | APSB25-118 | |
| Adobe Acrobat and Reader |  Medium Risk Medium Risk | Remote Code Execution Security Restriction Bypass | APSB25-119 | |
| Adobe Creative Cloud Desktop Application |  Medium Risk Medium Risk | Denial of Service | APSB25-120 |
Number of 'Extremely High Risk' product(s): 0
Number of 'High Risk' product(s): 0
Number of 'Medium Risk' product(s): 5
Number of 'Low Risk' product(s): 0
Evaluation of overall 'Risk Level': Medium Risk
Before installation of the software, please visit the vendor web-site for more details.
風險: 中度風險
類型: 操作系統 - 視窗操作系統
微軟已為產品提供本月保安更新:
| 受影響產品 | 風險程度 | 影響 | 備註 |
| 瀏覽器 | 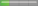 低度風險 低度風險 | 仿冒 | |
| 視窗 |  中度風險 中度風險 | 權限提升 遠端執行程式碼 資料洩露 阻斷服務 | CVE-2025-62221 正被廣泛利用。此漏洞存在於 Windows Cloud Files Mini Filter Driver。成功利用此漏洞的本地已授權攻擊者可以觸發權限提升。因此,該漏洞的風險等級被評為中度風險。 |
| 延伸安全性更新 (ESU) |  中度風險 中度風險 | 權限提升 資料洩露 遠端執行程式碼 仿冒 阻斷服務 | |
| 微軟 Office |  中度風險 中度風險 | 遠端執行程式碼 仿冒 | |
| Server Software |  中度風險 中度風險 | 仿冒 權限提升 | |
| Azure |  中度風險 中度風險 | 遠端執行程式碼 | |
| 其他 |  中度風險 中度風險 | 遠端執行程式碼 |
「極高度風險」產品數目:0
「高度風險」產品數目:0
「中度風險」產品數目:6
「低度風險」產品數目:1
整體「風險程度」評估:中度風險
在安裝軟體之前,請先瀏覽軟體供應商之網站,以獲得更多詳細資料。
RISK: Medium Risk
TYPE: Operating Systems - Windows OS
Microsoft has released monthly security update for their products:
| Vulnerable Product | Risk Level | Impacts | Notes |
| Browser | 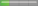 Low Risk Low Risk | Spoofing | |
| Windows |  Medium Risk Medium Risk | Elevation of Privilege Remote Code Execution Information Disclosure Denial of Service | CVE-2025-62221 is being exploited in the wild.. This vulnerability exist in Windows Cloud Files Mini Filter Driver. Successful exploitation of this vulnerability could allow a local authorized attacker to elevate privileges on the affected system. Hence, the risk level of this vulnerability is rated as Medium Risk. |
| Extended Security Updates (ESU) |  Medium Risk Medium Risk | Elevation of Privilege Information Disclosure Remote Code Execution Spoofing Denial of Service | |
| Microsoft Office |  Medium Risk Medium Risk | Remote Code Execution Spoofing | |
| Server Software |  Medium Risk Medium Risk | Spoofing Elevation of Privilege | |
| Azure |  Medium Risk Medium Risk | Remote Code Execution | |
| Other |  Medium Risk Medium Risk | Remote Code Execution |
Number of 'Extremely High Risk' product(s): 0
Number of 'High Risk' product(s): 0
Number of 'Medium Risk' product(s): 6
Number of 'Low Risk' product(s): 1
Evaluation of overall 'Risk Level': Medium Risk
Before installation of the software, please visit the vendor web-site for more details.
風險: 中度風險
類型: 操作系統 - Network
於 Fortinet 產品發現多個漏洞。遠端攻擊者可利用這些漏洞,於目標系統觸發遠端執行任意程式碼、權限提升、洩露敏感資料及繞過保安限制。
FortiAnalyzer
FortiAuthenticator
FortiManager
FortiOS
FortiPortal
FortiProxy
FortiSwitchManager
FortiWeb
FortiPAM
FortiSASE
FortiSRA
在安裝軟體之前,請先瀏覽供應商之網站,以獲得更多詳細資料。
安裝供應商提供的修補程式:
RISK: Medium Risk
TYPE: Operating Systems - Networks OS
Multiple vulnerabilities were identified in Fortinet Products. A remote attacker could exploit some of these vulnerabilities to trigge remote code execution, elevation of privilege, sensitive information disclosure and security restriction bypass on the targeted system.
FortiAnalyzer
FortiAuthenticator
FortiManager
FortiOS
FortiPortal
FortiProxy
FortiSwitchManager
FortiWeb
FortiPAM
FortiSASE
FortiSRA
Before installation of the software, please visit the vendor web-site for more details.
Apply fixes issued by the vendor:
風險: 中度風險
類型: 用戶端 - 瀏覽器
於 Mozilla Firefox 發現多個漏洞。遠端攻擊者可利用這些漏洞,於目標系統觸發仿冒、權限提升、遠端執行任意程式碼及繞過保安限制。
以下版本之前的版本﹕
在安裝軟體之前,請先瀏覽供應商之官方網站,以獲得更多詳細資料。
更新至版本:
RISK: Medium Risk
TYPE: Clients - Browsers
Multiple vulnerabilities were identified in Mozilla Firefox. A remote attacker could exploit some of these vulnerabilities to trigger spoofing, elevation of privilege, remote code execution and security restriction bypass on the targeted system.
Versions prior to:
Before installation of the software, please visit the vendor web-site for more details.
Apply fixes issued by the vendor:
風險: 中度風險
類型: 伺服器 - 其他伺服器
於 Synology 產品發現多個漏洞,遠端攻擊者可利用這些漏洞,於目標系統觸發阻斷服務狀況、權限提升及遠端執行任意程式碼。
在安裝軟體之前,請先瀏覽供應商之網站,以獲得更多詳細資料。
安裝供應商提供的修補程式:
RISK: Medium Risk
TYPE: Servers - Other Servers
Multiple vulnerabilities were identified in Synology products. A remote attacker could exploit some of these vulnerabilities to trigger denial of service condition, elevation of privilege and remote code execution on the targeted system.
Before installation of the software, please visit the vendor web-site for more details.
Apply fixes issued by the vendor:
風險: 中度風險
類型: 伺服器 - 網站伺服器
於 Apache 產品發現多個漏洞。遠端攻擊者可利用這些漏洞,於目標系統觸發阻斷服務狀況、繞過保安限制及敏感資料洩露。
在安裝軟體之前,請先瀏覽供應商之網站,以獲得更多詳細資料。
安裝供應商提供的修補程式:
RISK: Medium Risk
TYPE: Servers - Web Servers
Multiple vulnerabilities were identified in Apache HTTP Server. A remote attacker could exploit some of these vulnerabilities to trigger denial of service condition, security restriction bypass and sensitive information disclosure on the targeted system.
Before installation of the software, please visit the vendor web-site for more details.
Apply fixes issued by the vendor:
風險: 中度風險
類型: 用戶端 - 瀏覽器
於 Microsoft Edge 發現多個漏洞。遠端攻擊者可利用這些漏洞,於目標系統觸發阻斷服務狀況、權限提升、彷冒、遠端執行任意程式碼、洩露敏感資料及繞過保安限制。
在安裝軟體之前,請先瀏覽供應商之網站,以獲得更多詳細資料。
安裝軟件供應商提供的修補程式:
RISK: Medium Risk
TYPE: Clients - Browsers
Multiple vulnerabilities were identified in Microsoft Edge. A remote attacker could exploit some of these vulnerabilities to trigger denial of service condition, elevation of privilege, spoofing, remote code execution, sensitive information disclosure and security restriction bypass on the targeted system.
Before installation of the software, please visit the software vendor web-site for more details.
Apply fixes issued by the vendor:
Microsoft Edge 多個漏洞 發佈日期: 2025年12月12日 風險: 中度風險 類型: 用戶端 - 瀏覽器 於 Microsoft...